Several ISVs use installer technology that produces Setup.exe executable installers. These installers use a variety of command options but usually expose these options to the /? option.
Many Setup.exe installers were created by earlier versions of the InstallShield application-packaging utility. Prepare these installers for unattended installation by recording an installation script to be used to control the installer.
After the file is recorded, you can verify your responses by viewing the silent setup file in Notepad or Wordpad. Install with the silent option. Open a DOS window (Command Prompt). Type the directory path of the LanSafe Setup.exe. If spaces appear in the path, place quotes around the path. For example: 'C: LanSafe Installer Setup.exe'.
Common InstallShield Setup.exe options include:
- /s. Executes a recorded InstallShield (.iss) script
- /f. Locates the .iss script file for silent installation
- /r. Records the .iss script
- /SMS. Ensures the system does not disconnect from a network share during installation

To record and use an .iss script with Setup.exe
- Run Setup.exe with the /r option.
- Install the application normally.
- When the installation is complete, collect the script file (usually named Setup.iss) from the Windows directory. (Alternatively, use the /f1: option to designate a file name and location.)
- To deploy the application silently, use the /s option in the Command Prompt window:
Suppose you have an .EXE and you want to check if it has Command-Line Options. How can one know if the .EXE has this ability. In my case I know that Nir Sofers WebBrowserPassView.exe has the ability to start it via cmd.exe and WebBrowserPassView.exe /stext output.txt. But how can I find out if I don't know?
Tom Cerul6 Answers
The easiest way would be to use use ProcessExplorer but it would still require some searching.
Make sure your exe is running and open ProcessExplorer.In ProcessExplorer find the name of your binary file and double click it to show properties.Click the Strings tab.Search down the list of string found in the binary file. Most strings will be garbage so they can be ignored. Search for anything that might possibly resemble a command line switch.Test this switch from the command line and see if it does anything.
Note that it might be your binary simply has no command line switches.
For reference here is the above steps applied to the Chrome executable. The command line switches accepted by Chrome can be seen in the list:
Steven M. VascellaroInvoke it from the shell, with an argument like /? or --help. Those are the usual help switches.
Unless the writer of the executable has specifically provided a way for you to display a list of all the command line switches that it offers, then there is no way of doing this.
As Marcin suggests, the typical switches for displaying all of the options are either /? or /help (some applications might prefer the Unix-style syntax, -? and -help, respectively). But those are just a common convention.
If those don't work, you're out of luck. You'll need to check the documentation for the application, or perhaps try decompiling the executable (if you know what you're looking for).
Cody Gray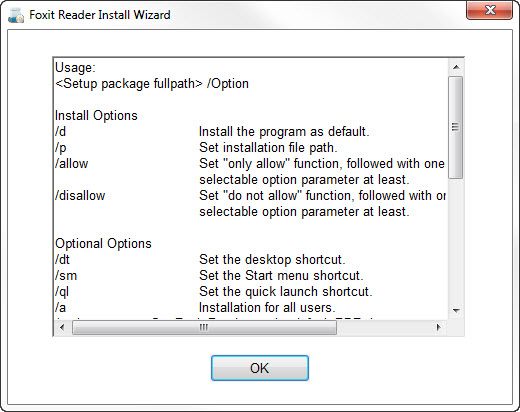 ♦Cody Gray
♦Cody GraySetup.exe Switches Office 2016
Just use IDA PRO (https://www.hex-rays.com/products/ida/index.shtml) to disassemble the file, and search for some known command line option (using Search...Text) - in that section you will then typically see all the command line options - for the program (LIB2NIST.exe) in the screenshot below, for example, it shows a documented command line option (/COM2TAG) but also some undocumented ones, like /L. Hope this helps?
Tom WenseleersTom WenseleersReally this is an extension to Marcin's answer.
But you could also try passing 'rubbish' arguments to see if you get any errors back. Getting any response from the executable directly in the shell will mean that it is likely looking at the arguments you're passing, with an error response being close to a guarantee that it is.
Failing that you might have to directly ask the publishers/creators/owners... sniffing the binaries yourself just seems like far too much work for an end-user.
Sysinternals has another tool you could use, Strings.exe
Example:
Adobe Setup.exe Switches
strings.exe c:windowssystem32wuauclt.exe > %temp%wuauclt_strings.txt && %temp%wuauclt_strings.txt